Even Cybersecurity Professionals Can Fall for a Phishing Attack
Dean Anderson, Commercial Director.
As the commercial director of an IT managed service provider that promotes “Secure IT By Design,” I’ve built my career on selling cybersecurity solutions. I regularly sit with clients, warning them about the dangers of phishing attacks. Yet, I recently fell victim to one myself. Thankfully, mine was during a planned phishing attack simulation, but I didn’t know this at the time!
I’m not alone. Troy Hunt (LinkedIn), the Founder and CEO of Have I Been Pwned and a Microsoft Regional Director & MVP, recently shared a story about a phishing ordeal. More details and a link to his comprehensive analysis of how he got tricked are provided later in this article.
If cybersecurity professionals like Troy Hunt and I can get fooled by phishing attacks, what does that say about non-expert IT users? And what can we learn from the expert experiences that allowed phishing attacks to succeed?
What is Phishing?
So that we’re all on the same page, let’s briefly recap what phishing means. It is:
An attempt by cybercriminals to trick individuals into providing sensitive information, most commonly their password, but also other information such as credit card numbers and other personal details, by pretending to be a trustworthy correspondent.
Phishing attacks typically arrive as emails that link to dummy websites that mimic legitimate organisations, making them difficult to distinguish from real communications. Once credentials get captured, attackers can escalate their access by impersonating users, deploying ransomware, or launching financial fraud. Phishing succeeds not by exploiting software vulnerabilities but human ones, such as our habits, assumptions, and tendency to trust. It is one of the most prevalent and deceptive forms of cyberattack.
Incidentally, the term itself is a neologism created in the 1990s by combining “fishing” with the “ph” spelling pattern commonly seen in hacker cultures.
My Experience: Caught by a Simulation I Should Have Spotted
I’ve spent years in front of clients as the commercial director of a managed IT services provider, urging them to take phishing threats seriously. I talk about it every week. I sell cybersecurity solutions built around the principle of “Secure IT by Design”. And yet, here I am confessing that I got fooled via a phishing simulation exercise. Our organisation ran the simulation to raise awareness about the phishing threat.
I received what appeared to be a legitimate email notification about my Office 365 password expiring. The email arrived in my inbox, and it looked plausible as it was about a password policy update. I recalled recent internal updates about password policies, and I didn’t think twice before clicking the link.
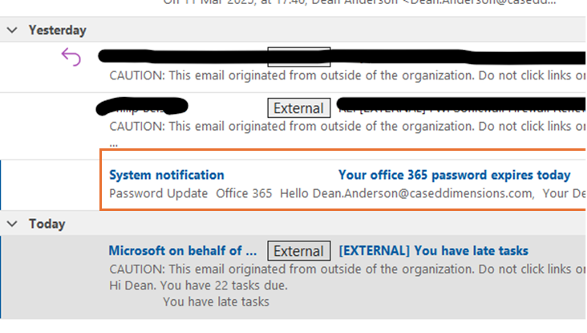
Figure 1: The phishing email in my inbox (other details redacted)
The login page the link took me to looked familiar. Microsoft branding and the kind of language you’d expect.
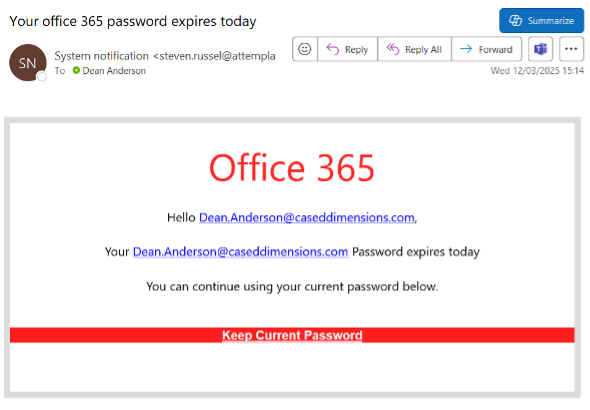
Figure 2: The page that the link in the phishing email opened
I wasn’t keen on resetting my password again, so I clicked the Keep Current Password link, thinking I was confirming my current one. This took me to what appeared to be a Microsoft login page.
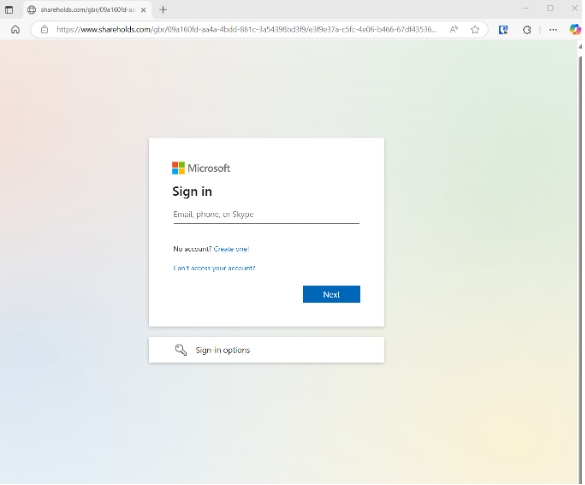
Figure 3: The login page that the Keep Current Password link opened
But wait! I noticed the domain on this login page: shareholds.com. Not Microsoft? That was the red flag that told me something was wrong. But it was too late. I realised I had been duped into clicking a potentially malicious link in a phishing simulation designed to raise staff awareness. Ironically, I was now a perfect example of how even professionals can be tricked.
What struck me most about my falling for this simulated attack was not the sophistication of the fake site but how reasonable the whole thing felt in the moment. And that it only took a single lapse in judgment for me to fail the simulated test.
I’m Not Alone: Troy Hunt’s Recent Experience
I’m not the only cybersecurity professional recently suffering a lapse in judgment regarding phishing emails. Troy Hunt, the founder of “Have I Been Pwned”, recently fell victim to a sophisticated phishing attack.
While jet-lagged and tired, he received a phishing email that looked like a legitimate Mailchimp email to his tired brain. After entering his credentials and two-factor authentication code on the fake phishing site, the attackers immediately logged into his real Mailchimp account and exported his entire mailing list of approximately 16,000 subscribers. Yikes! You can read his comprehensive mea culpa (and thoughts on what Mailchimp should maybe change) at https://www.troyhunt.com/a-sneaky-phish-just-grabbed-my-mailchimp-mailing-list/. It’s a long one, get the kettle on.
How to Defend Against Phishing Attacks
While these incidents show that nobody is immune to being fooled by phishing attacks, there are measures that organisations can take to reduce the threat and the risks that flow from a successful attack.
Stop Phishing Emails Before They Land
The most effective defence is prevention. Invest in email security tools that filter out phishing attempts before they even reach your users. Implement DMARC, SPF, and DKIM protocols to validate legitimate senders. Solutions such as secure email gateways, anti-spoofing technologies, and real-time link scanning can significantly reduce the number of phishing emails that reach your environment.
Build a Culture of Vigilance
Technology isn’t enough. Employees need regular awareness training, not once a year, but frequently to mirror the changing phishing tactics. Simulated phishing campaigns are a valuable tool in reinforcing vigilance, as my failure in our simulated attacks shows. However, leadership should pair them with encouragement and education rather than blame.
The key behavioural lesson? If something seems odd, out-of-place, or asks you to act urgently, then pause. Trust your instincts. Don’t click if you weren’t expecting a password change, invoice, or login prompt. Go to the website by manually entering the address in your browser (or use bookmarks for frequently visited websites).
Adopt a Zero Trust Mindset
We hear it all the time in security circles: use zero trust! However, it’s essential to understand that zero trust is not merely an architectural model. It’s also a state of mind that promotes a question-everything methodology. Assume nothing is safe just because it looks legitimate. My mistake was trusting too easily. Trusting the branding, trusting the familiarity, and ultimately trusting that something like that couldn’t fool someone like me. That was my biggest mistake.
Final Thoughts
My experience and Troy Hunt’s recent incident serve as a potent reminder that cybersecurity is not just about technical knowledge but also constant vigilance. Even those who work in cybersecurity and understand the technical aspects can get tricked when our guard is down.
The lesson I learned, as the current IT industry says, is “Zero Trust.” If you don’t like the look of something, don’t engage with it, full stop. Also, engage with a trusted IT security provider, like Cased Dimensions, who can help reduce the chances of this kind of deception getting into your inbox in the first place.
No matter how experienced you are, remember: the cybercriminals only need to be right once, while we need to be right every time.

